Cybersecurity firm FireEye made Malaysian businesses anxious when it warned they could be the next targets of state-sponsored hackers. The new Malaysian government’s unfavourable stance towards China’s Belt and Road Initiative (BRI) projects may attract the attention of cyber espionage hackers.
FireEye said in a statement that its analysts observed a pattern of targeting by China-based groups and others against organisations with links to the BRI. These even include countries that are close allies to China. The company recently reported widespread compromise of the Cambodian political system by TEMP.Periscope, a group of suspected cyber espionage actors believed to be from China.
It also pointed to APT 30, a hacker group which has been targeting Southeast Asia and India as far back as 2004. It is especially active during ASEAN summits and when issues appear, such as territorial disputes involving China and Southeast Asian countries and India. Even media organisations and journalists covering regional topics are targeted.
FireEye believes the BRI will spur regional cyber threat activity to gain information and intelligence on individual projects and agreements, from both China-based hackers targeting countries in the region and other nation-state hackers targeting Chinese organisations.
Expected targeted sectors are regional governments, academia and think-tanks, transportation, construction, manufacturing, energy, mining and finance, it said.
“One reason cyber espionage is prevalent in Southeast Asia is because most organisations are not able to detect the intrusion,” said Sandra Joyce, vice president and head of global intelligence operations at FireEye in a statement.
Speed is of the essence
The M-Trends 2018 report by Mandiant Consulting states that Asia Pacific companies took 498 days to detect cyberattacks last year, compared to 75.5 days in the Americas and 175 days in Europe, the Middle East and Africa. Companies that were compromised were more likely to be targeted again by multiple attackers.
Nick Fitzgerald, senior research fellow with cyber security firm ESET, cautioned against making speculations as the mechanics of cyberattacks vary considerably and no specific attack was detailed in the warning.
However, he conceded that “if you are a valuable enough target, a sufficiently motivated adversary will probably compromise your computer systems.”
There is a saying among computer security circles that there are two kinds of organisations: those that have been hacked and those that do not know it yet. Even if a cyberattack is imminent – or under way – it will likely be under the radar to maximise the length of time it has to spread through its victims’ networks. The longer they remain undetected, the more valuable data they can gain access to. They can even gain control to critical systems.
 Source: Australian Strategic Policy Institute
Source: Australian Strategic Policy Institute
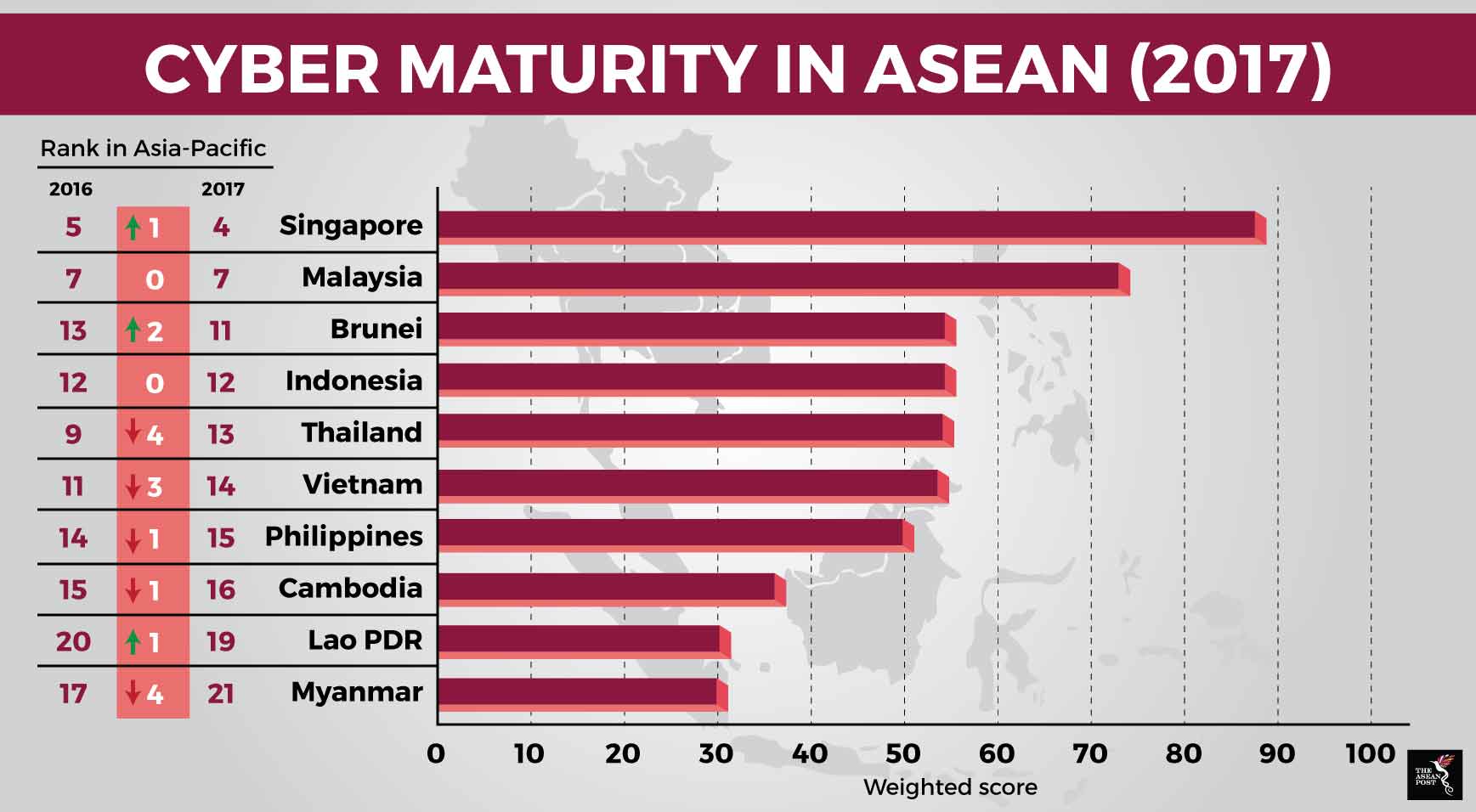
The International Cyber Policy Centre of the Australian Strategic Policy Institute (ASPI) assesses Asia-Pacific countries’ readiness to the challenges and opportunities of cyberspace. It includes governance, legislation, law enforcement and cyber security issues, among others in its assessment.
Is anyone safe?
In its latest report, Cyber Maturity in the Asia Pacific Region 2017, Singapore came out tops among ASEAN nations, rising one level from 2016. It is ranked fourth behind the United States (US), Japan and Australia.
This is worrisome as “Fortress Singapore” was breached in July this year, when its largest healthcare group, SingHealth, was hacked. Its fellow ASEAN members may not be as resilient, nor have sufficient resources for cybersecurity. In some of these countries, important physical infrastructure such as power generation, roads and hospitals, may have to take precedence over cybersecurity.
Espionage was the suspected reason behind the SingHealth breach as the Singapore Prime Minister’s data was specifically searched numerous times, “but what if some hackers found a vulnerability and decided to search for the most famous Singaporean name they could think off?” asked Fitzgerald.
“Or perhaps the searches for the Prime Minister’s data and the large amount of ‘stolen’ data are ‘noise’ or smokescreens to conceal the real target of the attack if and when the breach was discovered?” he added.
Without further indications or evidence, the true motives of the hackers behind the SingHealth attack, and the warning of impending attacks in Malaysia and other BRI-linked countries, for that matter, are purely speculation.
Related articles:
