Technology is evolving rapidly in unthinkable ways. Amazing tools and resources are created by technology, resulting in many new ways of how we can stay connected with our families and friends. Along with this positive development, new types of cybersecurity risks have also begun to evolve and grow.
Facebook is the largest social media network with 2.41 billion active users all over the world. Did you know, however, that Facebook – like any other social media platform – leaves us vulnerable to cyberattacks?
Experts confirmed that social media plays a growing role in perpetuating cybercrime. Each year, social media-enabled crimes contribute at least US$3.25 billion to the cybercrime economy.
The main reason why social media is prone to attacks is because these sites make it very easy for people to share and pass on just about any form of information – and that, unfortunately, includes malware.
According to a popular daily in the United Kingdom (UK), a 2019 cyberattack resulting in a data breach affected more than 267 million United States’ (US) Facebook users. Their personal information was exposed on the dark web via an unsecured database.
The dark web is everything that is unreachable through our standard search engines like Google Chrome or Mozilla Firefox. You can trace any type of information that is inaccessible via standard search engines and from the dark web.
Local media in the UK quoted a scary incident in which a security researcher at popular pro-consumer website, Comparitech found that his database was left open for 14 days on the dark web. The researcher also confirmed that individuals from Vietnam were responsible. So, who should be held responsible for this crime? Mark Zuckerberg or the hackers? Both.
Experts believe that no password or security protection was used to protect the database.
In 2018, the now infamous data analytics firm, Cambridge Analytica harvested millions of Facebook users’ information to create a prevailing predictive software programme – which at the time was the biggest data breach case ever. This breach raised major concerns among Facebook users on how well the tech company was protecting the privacy of their data.
A data breach is just one of the many perilous cyberattacks today that can be used for spyware – designed to gather data from users’ computers. Another is phishing – a method where criminals gain access to personal information – allowing them to do such things as steal money from bank accounts.
Another recent data breach in the UK resulted in the addresses of more than a thousand New Year honours recipients being published online on a government website for about one hour. This disclosure put all the affected individuals in a vulnerable position and was a complete disaster.
The UK Cabinet Office was criticised for this “farcical and inexcusable mistake” and was scrutinised under the new Data Protection Act that was passed by the UK government in 2018. The Act controls how personal information is used by organisations, businesses or the government.
Best practices
A company must first ensure that all the software used to operate the business is updated and patched regularly to avoid weak spots for hackers to exploit. Throughout its lifetime, software will collide with glitches named bugs. This is where a patch is utilised to fix those glitches.
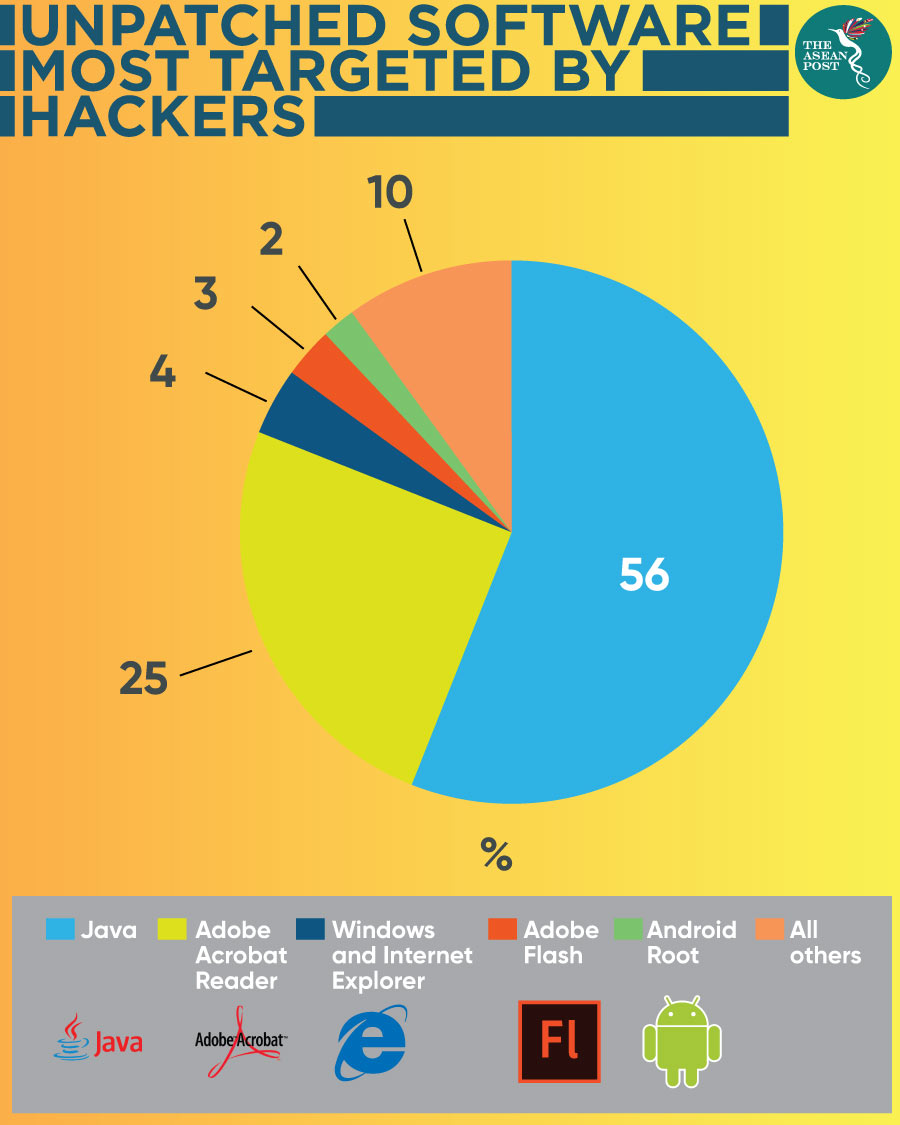
Researchers found that unpatched software most targeted by web exploits are – Java (56 percent of the time), Adobe Acrobat Reader (25 percent), Windows and Internet Explorer (four percent), Adobe Flash (three percent), Android Root (two percent), and Others (10 percent).
New and enhanced features of the software need to be updated frequently towards better security through stable software and speed enhancements. Although updating software is galling, it can improve the company’s experience in the long run and guarantee that technology is being used securely.
From a social media perspective, users should always be very cautious with the information they publish on their social media accounts. Avoid oversharing information like full names, home addresses or phone numbers. This information, also known as Personal Identifiable Information (PII), can provide instant access for attackers to gain access to financial accounts, credit records and other assets.
Did you know that using public Wi-Fi is actually risky?
Although public Wi-Fi is functional in connecting entire cities and providing communities with better services, there are threats lurking in the background on public Wi-Fi – ready to attack unlucky users.
A study conducted by the US-based Identity Theft Resource Center, a non-profit organisation that provides support for victims of identity theft, showed that about 40 percent of people were unconcerned about using public Wi-Fi. One of the biggest threats with free Wi-Fi is the ability for attackers to place themselves between you and the connection point – referred to as Man-in-the-Middle (MiTM) attacks.
Imagine, while sipping a hot cappuccino at your favourite cafe, you are wiring some money to your parents via an online banking system using the café’s public Wi-Fi. Technically, if you are being attacked by a MiTM, your computer is essentially connected to the attacker’s computer, making you falsely believe that they are the server (in this case the online banking system). Then, the attacker pretends to be you and connects to the real server, relaying information both ways.
The attacker not only “sees” what you are doing, but can also modify your information and take advantage of it for personal gain like performing fraudulent online transactions and transferring money out of your bank account.
However, if you really need to connect to public Wi-Fi, especially when you are in another country, here is what you can do: You should consider using a Virtual Private Networks (VPN) to connect to the Wi-Fi. The main job of a VPN is to secure your connection by sending your data through an encrypted tunnel.
By doing so, the chances of the internet service provider or any third-party attacker “seeing” or modifying the information you send over the network is smaller. According to tech-experts, the most secure VPN providers with top-notch encryption are ExpressVPN, NordVPN, and VyprVPN and can be purchased online.
Overall, it is vital to understand the many threats that could compromise the online security of your personal information, especially in this connected world. If you think no one would be interested in your personal information, think again. Anyone can be a victim.
As the saying goes, “prevention is better than the cure” – stay up-to-date and ensure all your devices are fortified with suitable security features, as well as make these practices part of your daily online routine.
Nurafifah Mohammad Suhaimi is a Research Assistant at EMIR Research in Malaysia, an independent think tank that is focused on strategic policy recommendations based on rigorous research.
Related articles:
